-
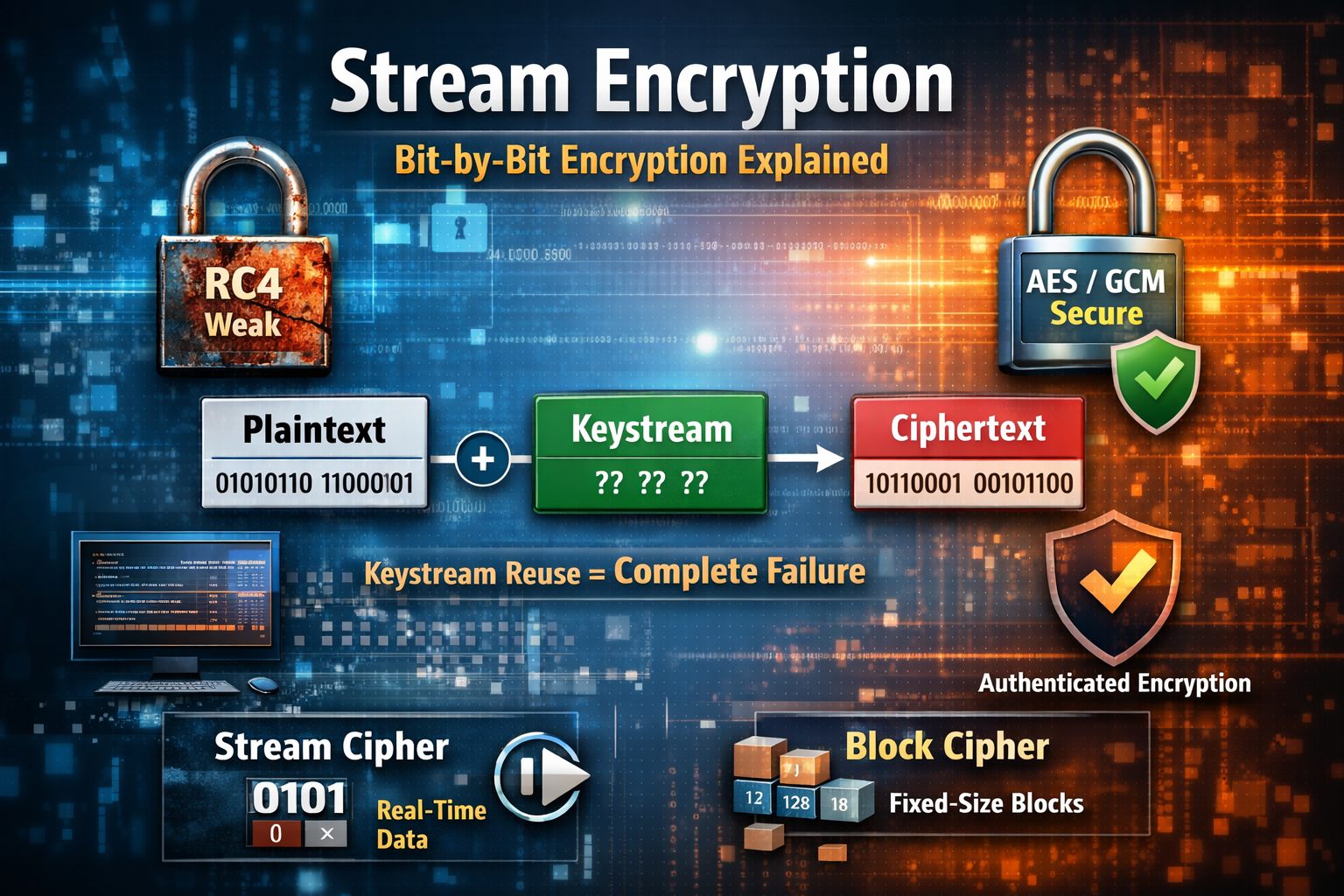
Don’t want the in depth guide? Check out the quick break down hereBlock Cipher Modes of Operation Explained: ECB vs CBC vs CTR vs GCM (CISSP Guide) Block cipher modes of operation define how a block cipher repeatedly transforms chunks of data to achieve secure encryption beyond a single block. A block cipher alone (like…
-
The software supply chain is under attack. Discover how to mitigate NPM risks, ransomware, and third-party threats with proactive Shift Left security.
-
Is your risk matrix failing? Learn how to turn Impact × Likelihood into actionable SLAs, owners, and measurable progress that drives real fixes.
-
Get daily cybersecurity updates! Explore emerging threats, new vulnerabilities, and the latest security news to stay ahead in the evolving digital landscape.
-
May 2025 AI saw huge leaps! Explore OpenAI’s new models, Anthropic’s agent breakthroughs, and vital discussions on AI ethics. Get your essential update now.
-
Discover Microsoft’s May 2025 updates on AI Copilot, major security enhancements, new vulnerabilities, and AI reasoning. Get the essential details here!
-
Contact Us for Questions or Advice! We want our Site prepped and ready prior to Launch! Get in Touch with Our Team Today! Your feedback is crucial to our mission. Feel free to use what ever method is easier. Email: Info@ITKnowledgeBases.comor use the form below!