Microsoft’s February 2026 Patch Tuesday introduced a significant zero-day vulnerability tracked as CVE-2026-21510, which was both publicly disclosed before a patch and actively exploited in the wild.
1. Summary: What Is CVE-2026-21510?
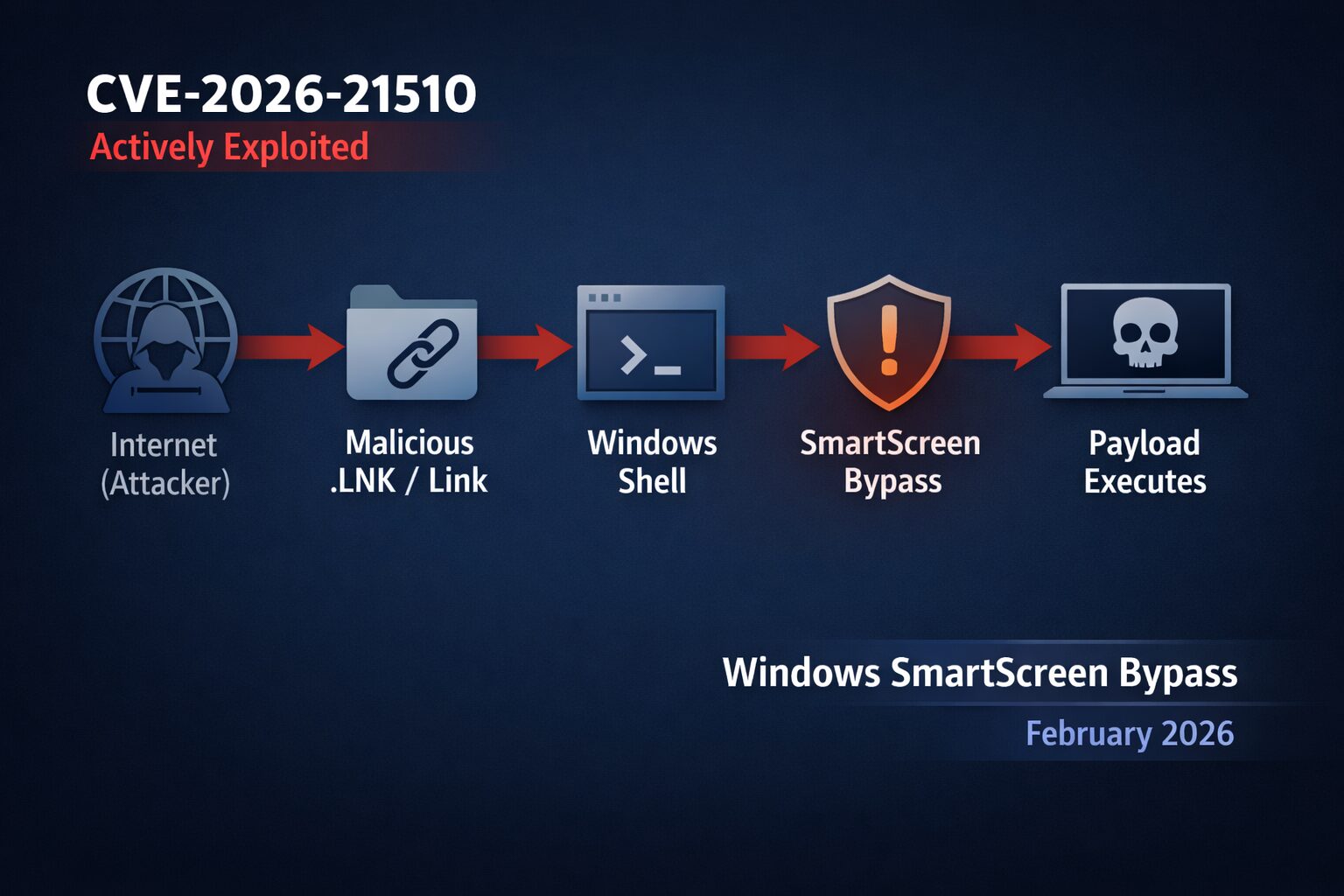
CVE-2026-21510 is a Windows Shell Security Feature Bypass vulnerability with a CVSS v3.1 base score of 8.8. It affects Microsoft Windows operating systems and allows attackers to circumvent built-in protections such as Windows SmartScreen and other Shell warning prompts. This bypass enables attacker-controlled content to execute without triggering typical safety dialogs.
Unlike many vulnerabilities that require deep system access, this flaw can be exploited with no privileges — all it takes is convincing a user to open a malicious link or shortcut.
2. When Was It Disclosed?
This vulnerability was publicly published on February 10, 2026, as part of Microsoft’s February 2026 Patch Tuesday release. It was also added to the U.S. Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) Catalog on the same day, underscoring its in-the-wild impact.
According to the NVD (National Vulnerability Database), the NVD entry and metadata for CVE-2026-21510 were published on February 10, 2026, then updated the following day.
3. Technical Impact
- Component Affected: Windows Shell — the core module handling the graphical interface and file execution logic.
- Attack Vector: Requires user interaction — typically a crafted link or
.lnkshortcut. - Outcome: Bypasses SmartScreen and Shell warnings, enabling execution of untrusted content.
- Exploitability: High — points of entry are common (email links, downloads).
4. Exploitation and Public Exposure
This vulnerability was actively exploited before Microsoft issued a patch, meaning adversaries already had ways to weaponize it in real attacks prior to formal mitigation.
Because the flaw doesn’t require elevated privileges and abuses existing functionality, it fits naturally into phishing and malware delivery campaigns where attackers trick users into initiating the exploit themselves.
Check out the phishing scanner to avoid clicking on a sketchy link!
Furthermore, multiple industry sources noted that three of the six zero-day flaws patched in February 2026 (including CVE-2026-21510) were publicly disclosed prior to the update — implying exploit details were circulating among researchers and threat actors.
Public exploit code and research analysis tend to emerge quickly for security bypass bugs like this because they are lower complexity and highly relevant to common attack patterns.
5. Affected Versions
While specific vendor advisories list variant details, this flaw impacts all currently supported Windows versions, including:
- Windows 10 builds (including 1607, 1809, 21H2, 22H2)
- Windows 11 variants
- Multiple Windows Server releases
(These affected platforms were detailed by multiple industry summaries and NVD records.)
6. Why It Matters
CVE-2026-21510 is particularly noteworthy because:
- It bypasses fundamental security mechanisms (SmartScreen & Shell prompts).
- Exploitation requires only basic social engineering.
- It was in the wild before a patch existed, making it a genuine zero-day.
- It is part of a rare group of zero-day flaws fixed in one Patch Tuesday.
Security feature bypasses like this are often used to drop malware or evade endpoint protection, because they neutralize the OS’s first line of defense against untrusted content.
7. Mitigation Recommendations
To protect environments:
- Apply the February 10, 2026 cumulative updates immediately across all Windows endpoints.
- Verify that SmartScreen and system integrity protections are enabled by policy.
- Educate users on avoiding suspicious links and attachments — user interaction is required for exploitation. (Bonus points for using our phishing scanner)
- Review IDS/IPS signatures and endpoint detection alerts for bypass patterns.
Because this CVE is in CISA’s KEV catalog with a remediation deadline (March 3, 2026), organizations tied to U.S. federal requirements must treat this as a compliance priority.
8. Related Vulnerabilities in the Same Release
CVE-2026-21510 was part of a broader February 2026 Patch Tuesday that included six actively exploited zero-days, three of which were publicly disclosed prior to patching. Other notable flaws patched alongside it include:
- CVE-2026-21513: MSHTML (Trident) security feature bypass.
- CVE-2026-21514: Microsoft Word security feature bypass.
- CVE-2026-21519: Desktop Window Manager local privilege escalation.
- CVE-2026-21533: RDP elevation of privilege.
- CVE-2026-21525: DoS in Remote Access Connection Manager.
This cluster of exploits underscores how attackers continue leveraging social engineering and bypass logic to compromise Windows systems.
Conclusion
CVE-2026-21510 stands out in 2026’s Patch Tuesday as a publicly disclosed, actively exploited zero-day that undermines key Windows protections while requiring minimal technical complexity to abuse. Organizations should treat this vulnerability with urgency because of its wide reach, real-world exploitation, and position in CISA’s KEV catalog.
Leave a Reply
You must be logged in to post a comment.