Network segmentation and network isolation are foundational concepts in secure network architecture. They’re often discussed together because both reduce risk, but they are not interchangeable and serve very different purposes in a security strategy.
This matters for technical professionals who design, assess, or secure enterprise networks. Misunderstanding the distinction can lead to poor architecture decisions, ineffective risk controls, and unnecessary complexity.
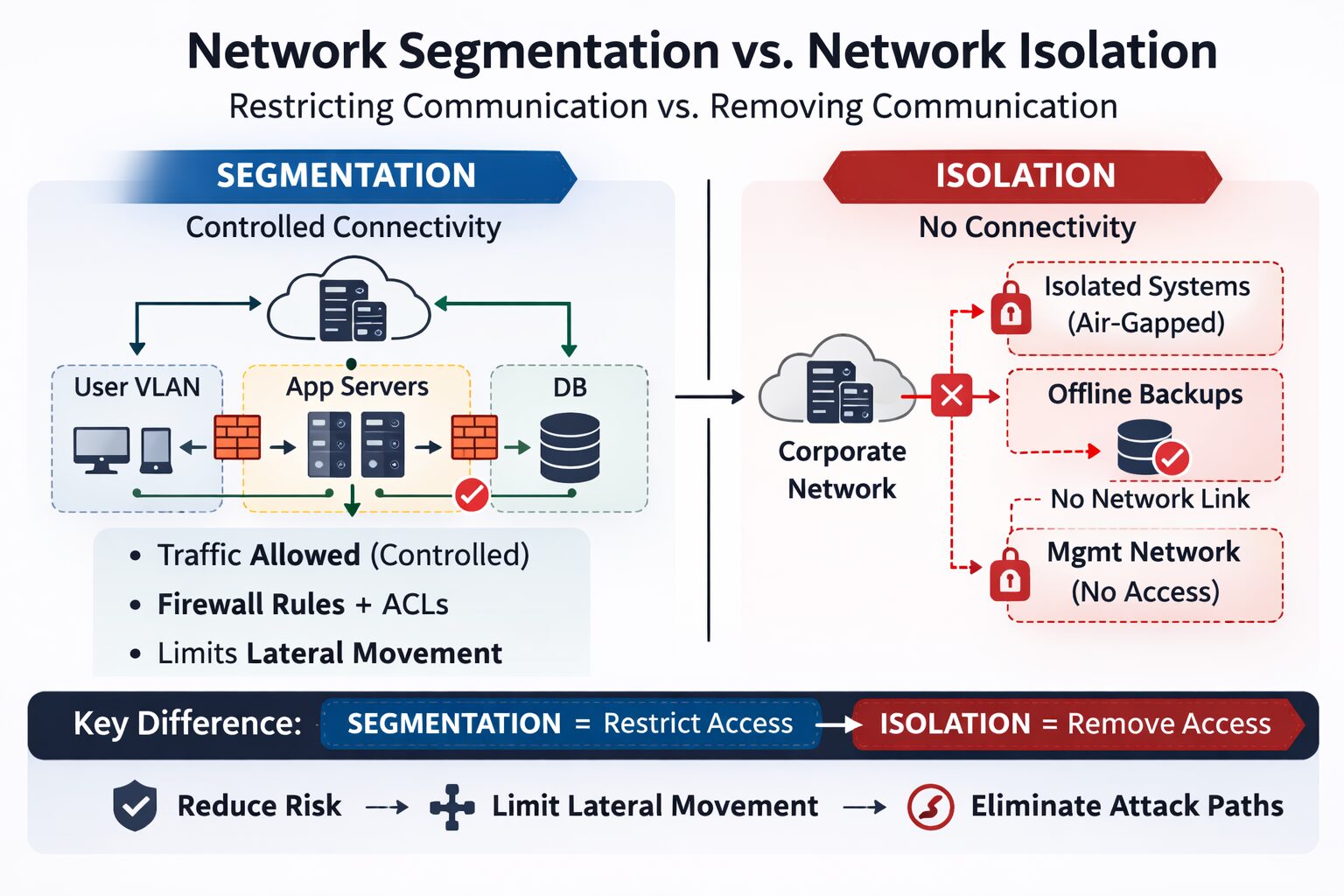
What Network Segmentation Really Is
Network segmentation is the architectural practice of dividing a network into smaller subnetworks or “segments” so that traffic can be controlled between them. It’s a fundamental defense-in-depth control and one of the primary ways organizations limit an attacker’s ability to move laterally after a breach.
Segmentation isn’t just about splitting up IP ranges — it’s about creating security zones with enforced traffic policies between those zones. You use routers, firewalls, VLANs, or software-defined controls to decide what can talk to what.
Key properties of segmentation:
- Divides networks into smaller trust zones with policy-enforced boundaries.
- Controls east-west (lateral) traffic and restricts broad broadcast domains.
- Improves monitoring and performance because each zone has fewer hosts and clearer traffic patterns.
- Supports Zero Trust by minimizing implicit trust between systems.
Common segmentation tools include VLANs, ACLs, firewalls, and logical subnet boundaries. When implemented correctly, segmentation slows compromise propagation and forces attackers through multiple enforcement points.
Important nuance: being on different subnets or VLANs alone doesn’t achieve segmentation unless you also enforce granular traffic controls between those subnets.
What Network Isolation Really Is
Network isolation goes further than segmentation: it removes or greatly restricts communication pathways between systems, zones, or environments. It’s not about controlling traffic — it’s about eliminating it where it isn’t needed.
Isolation is a proactive boundary control. If a segment doesn’t need to communicate at all with another part of the network, isolation eliminates that attack vector entirely.
Practical examples include:
- Air-gapped systems — systems with no network interfaces connected to other networks. This prevents remote attacks entirely.
- Offline backup environments — no routing, no remote access, only manual data movement.
- Dedicated management networks with no access from user or production zones.
Isolation drastically reduces the attack surface but comes with operational tradeoffs. It makes integration and automated workflows harder and often requires manual processes for data transfer or management.
Segmentation vs. Isolation: Core Differences
| Attribute | Network Segmentation | Network Isolation |
|---|---|---|
| Connectivity | Allowed and controlled | Eliminated where unnecessary |
| Purpose | Reduce impact of compromise | Remove paths of attack |
| Typical Tools | VLANs, ACLs, firewalls | Air gaps, physically separated networks |
| Risk Boundary | Managed via policy | No network path exists |
| Operational Impact | Moderate | High |
Segments assume communication is necessary but should be restricted. Isolation assumes communication is unnecessary or unacceptable from a security perspective.
In other words: segmentation restricts; isolation removes.
How the Concepts Are Used in Practice
Segmentation in Enterprise Networks
Enterprises commonly use segmentation to:
- Separate production, development, and test environments.
- Restrict access to sensitive systems (finance, HR).
- Control traffic between IoT networks and core infrastructure.
- Divide hybrid cloud and on-premise components with virtual network policies.
Effective segmentation requires ongoing policy management, monitoring, and validation. Misconfigured ACLs or overly permissive rules negate much of the benefit.
Isolation for High Assurance
Isolation is typical in high-assurance or compliance-driven contexts where the cost of a compromise is intolerably high:
- Industrial control systems that must not interface with corporate networks.
- Classified networks with strict separation requirements.
- Critical backups that must be unreachable except via secure offline processes.
Here, the goal isn’t performance or convenience — it’s assurance that no network path exists for unauthorized access.
How These Fit in Modern Security Architectures
Segmentation is a core part of Zero Trust architectures, which assume breach and enforce least-privilege everywhere. It turns broad, flat networks into policy-enforced security domains.
Isolation is used where Zero Trust still cannot provide sufficient assurance, or where connectivity is genuinely unnecessary.
Many organizations employ both: segmentation to control normal network traffic and isolation to provide hardened enclaves for critical systems.
Common Misconceptions
- “VLANs alone achieve segmentation.”
VLANs need policy enforcement between them; they don’t automatically stop all traffic. - “Segmentation equals isolation.”
Segmentation still allows controlled communication; isolation eliminates it. - “Isolation is always better.”
Isolation increases security but often reduces efficiency and requires operational workarounds.
Final Notes for Security Professionals
- Segmentation is foundational for reducing risk in modern networks — especially in hybrid, cloud-centric organizations.
- Isolation is a specialized tool for situations where connectivity risk cannot be tolerated.
- Both are architectural decisions — choose based on risk tolerance, operational needs, and compliance requirements.
for more like this check out What is the CISSP Certification? Is it Worth It in 2026?
Leave a Reply
You must be logged in to post a comment.